Use Let’sEncrypt SSL Certificates for Spinnaker and Make your CD Secure
Let’s Encrypt is a free, automated, and open certificate authority (CA) brought to you by the nonprofit Internet Security Research Group (ISRG). It provides free SSL certificates but does not provide DNS routes for the domain address to IP address. Currently, we use GoDaddy certificates, ( along with their DNS service) which is a paid service.
This blog is proof of concept, for using letsencrypt certificates.
(// for https one needs SSL certificates. Ways to get an SSL certificate from Let’s encrypt for free)
How to create a certificate issued by LetsEncrypt in Kubernetes?
Prerequisites:
- cert-manager,
- kubernetes,
- DNS (to route traffic from your domain name to your ingress controller IP address GoDaddy, route53..etc),
- nginx ingress controller.
Steps:
- Create issuer for letsencrypt prod using kubectl create -f, change the email address, and optionally the name of the secret.
— Create a yaml file and copy the following code —
apiVersion: cert-manager.io/v1
kind: Issuer
metadata:
name: letsencrypt-prod
spec:
acme:
# The ACME server URL
server: https://acme-v02.api.letsencrypt.org/directory
# Email address used for ACME registration
email: gopal.jayanti@opsmx.com
# Name of a secret used to store the ACME account private key
privateKeySecretRef:
name: letsencrypt-prod
# Enable the HTTP-01 challenge provider
solvers:
– http01:
ingress:
class: nginx
- Create sample test app deployment, svc, and ingress
— Refer to the yaml code given below for deployment —
apiVersion: apps/v1
kind: Deployment
metadata:
name: kuard
spec:
selector:
matchLabels:
app: kuard
replicas: 1
template:
metadata:
labels:
app: kuard
spec:
containers:
– image: gcr.io/kuar-demo/kuard-amd64:1
imagePullPolicy: Always
name: kuard
ports:
– containerPort: 8080
—
— Refer to the yaml code given below for service —
apiVersion: v1
kind: Service
metadata:
name: kuard
spec:
ports:
– port: 80
targetPort: 8080
protocol: TCP
selector:
app: kuard
—
— Refer to the yaml code given below for ingress —
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: kuard
annotations:
kubernetes.io/ingress.class: “nginx”
cert-manager.io/issuer: “letsencrypt-prod”
spec:
tls:
– hosts:
– letstest.opsmx.com
secretName: mytls
rules:
– host: letstest.opsmx.com
http:
paths:
– path: /
backend:
serviceName: kuard
servicePort: 80
—-
Make sure of the correct hostname and that this hostname has an A record or CNAME in the DNS provider, and this record points to the ingress controller service public IP address.
- Check if the certificate is created
kubectl -n lets get cert
NAME READY SECRET AGE
mytls True mytls 11m
If the Ready state is not ‘true’, try to describe the certificate, certificate request, challenge, and order.
- Check from the browser, go to https://letstest.opsmx.com
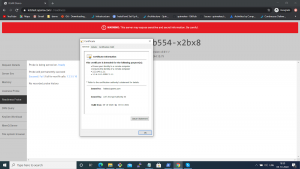
Readiness Probe-Check if the certificate is created
References:
https://cert-manager.io/docs/tutorials/acme/ingress/
(https://docs.cert-manager.io/en/release-0.11/reference/clusterissuers.html)
The above configuration was a generic example. Given below is the configuration for Spinnaker services.
For Spinnaker, one can use an ingress similar to the one used for the nginx service as above.
The ingress yaml is given below:
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
annotations:
artifact.spinnaker.io/location: oes
artifact.spinnaker.io/name: spingressui
artifact.spinnaker.io/type: kubernetes/ingress
kubernetes.io/ingress.class: nginx
moniker.spinnaker.io/application: helmdemo
moniker.spinnaker.io/cluster: ingress spingressui
nginx.ingress.kubernetes.io/use-regex: “true”
cert-manager.io/issuer: “letsencrypt-prod”
labels:
app.kubernetes.io/managed-by: spinnaker
app.kubernetes.io/name: helmdemo
name: letsencrypt-ingress
spec:
backend:
serviceName: spin-deck
servicePort: 9000
rules:
– host: demo.opsmx.com
http:
paths:
– backend:
serviceName: spin-gate
servicePort: 8084
path: /login
– backend:
serviceName: spin-gate
servicePort: 8084
path: /auth/*
tls:
– hosts:
– demo.opsmx.com
secretName: mytls
Output:
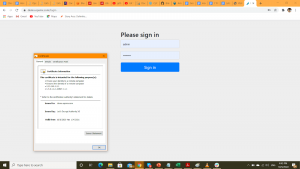
Check the certificate for the demo spinnaker instance
Conclusion:
Kubernetes is configured to use Let’s Encrypt as a certificate manager that enables your Spinnaker services to establish their identity and communicate securely over the network with other services or clients internal or external to the cluster.
