Continuous Deployment to Kubernetes using GitHub triggered Spinnaker pipelines
This blog explains how to configure Spinnaker v1.19.1 to trigger pipelines based on commits to a GitHub repository and inject changed GitHub files as artifacts into the Spinnaker pipeline for Continuous Deployment on Kubernetes.
- Prerequisites
- Configure GitHub webhooks
- Configure a GitHub artifact account
- Configure Spinnaker Pipeline Trigger
- Verification
1. Prerequisites
- A GitHub repository either under your user or in an organization or user’s account that you have permission to publish commits to Prepare a GitHub repository with some source code to build and it must contain some source code to build artifact.
- A running Spinnaker instance
2. Configure GitHub Webhook for Spinnaker
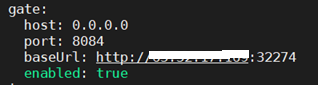
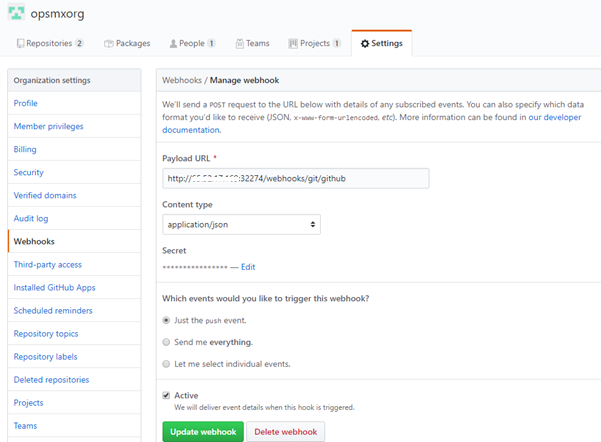
Under the GitHub repository, navigate to Settings -> Webhooks -> Add Webhook. Here, provide the following values to the form shown below: Payload URL: The Payload URL should be $ENDPOINT/webhooks/git/github We need Spinnaker’s API running on an endpoint that is publicly reachable. This is required to allow GitHub’s webhooks to reach Spinnaker. If you’re unsure of what your Spinnaker API endpoint is, check the value of services.gate.baseUrl in ~/.hal/$DEPLOYMENT/staging/spinnaker.yml. The value of $DEPLOYMENT is typically default.
Example:
Content-type: The value should be ‘application/json’
Secret: The value is up to you, and must be provided to any GitHub webhooks triggers that you configure within Spinnaker. It’s used to ensure that only GitHub can trigger your pipelines, not an imposter.
3. Configure a GitHub Artifact Account for Spinnaker
Spinnaker can be configured to listen to changes to a repository in GitHub. These steps show you how to configure a GitHub artifact account so that Spinnaker can download files from GitHub.
- Downloading Credentials Start by generating an access token for GitHub. The token requires the repo scope. Here Create an access token for GitHub by following the below link: https://help.github.com/en/articles/creating-a-personal-access-token-for-the-command-line Generate an Access token for GitHub account and downloaded credentials are saved in ‘github_token_file‘. TOKEN_FILE=/home/opsmxuser/dvrs/github/github_token_file
- Editing Artifact Settings in Spinnaker Config Enable GitHub artifact support and add an artifact account:
TOKEN_FILE=/home/opsmxuser/dvrs/github/github_token_file ARTIFACT_ACCOUNT_NAME=dvr-github-artifact-act $ hal config features edit –artifacts true $ hal config artifact github enable $ hal config artifact github account add $ARTIFACT_ACCOUNT_NAME –token-file $TOKEN_FILE $ hal deploy apply
4. Configure Spinnaker Pipeline Trigger deployments on Kubernetes
Configure Spinnaker pipeline to be triggered by a GitHub commit:
4.1 Configure Spinnaker pipeline to trigger with changes in GitHub and make deployments on Kubernetes
- In Pipeline configuration, click the Configuration stage on the far left of the pipeline diagram.
- Click on Add Artifact under the Expected Artifacts section.
- Select an artifact account that was added earlier (3.2) from the Account drop-down list and enter the File Path field.
- Select ‘Use Default Artifact’ and specify the artifact account that was added earlier (3.2) from the Account drop-down list and the ‘Content URL’. Here the ‘Content URL’ is used as: https://api.github.com/repos/opsmxorg/samplerepo/contents/manifest.yaml
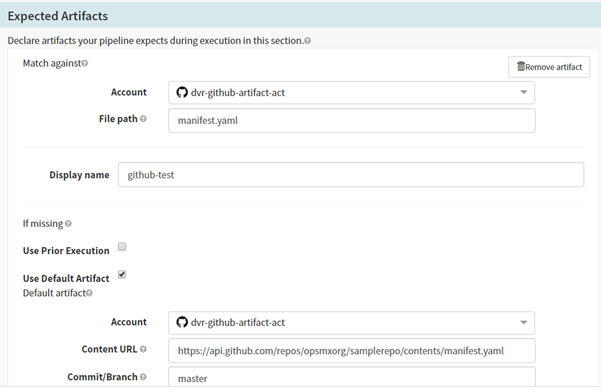
Add expected artifacts in Spinnaker pipeline for deployments on Kubernetes
- Add one more Artifact Account for Docker-Registry as an account and the Docker image name that we want to trigger on changes to.
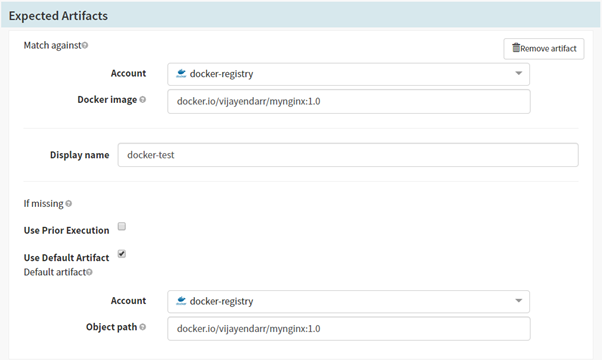
Add artifact account in Spinnaker pipeline for deployments on Kubernetes
- Update Automated Triggers details
- Click Automated Triggers.
- In the Type field, select Git.
- In the Repo Type field, select Github.
- In the Organization or User field, enter the organization value of your Git repository.
- In the Project field, enter the Github repository name.
- Specify the appropriate branch details for the Branch.
- Provide the Secret value that was entered during GitHub Webhook configuration at Section #2.
- Select the Display name for Artifact Constraints which was generated in the Expected Artifacts section.
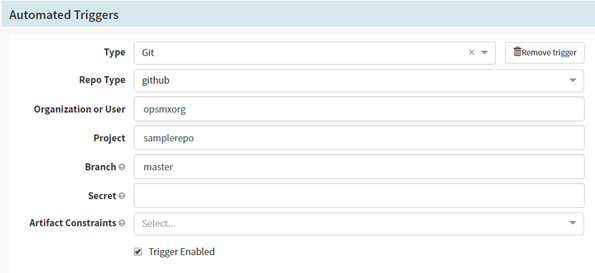
Automated Trigger in Spinnaker pipeline for deployments on Kubernetes
4.2 Configure Deploy Manifest in Spinnaker pipeline for deployments on Kubernetes
Select the Deploy (Manifest) stage by specifying the manifests statistically.
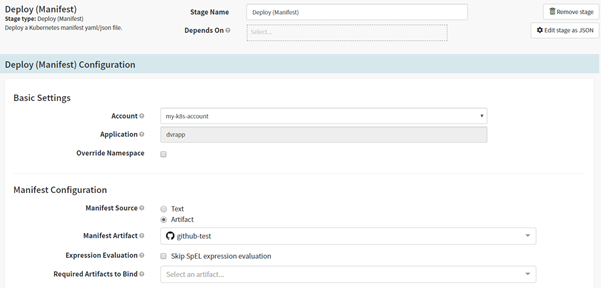
Configure Deploy Manifest in Spinnaker pipeline for deployments on Kubernetes
5. Verification of the Spinnaker deployments on Kubernetes
Make a change into the repository (https://github.com/opsmxorg/samplerepo.git) for specified Filepath(example: manifest.yaml) and ensure Spinnaker’s pipeline is auto-triggered. This can also be verified under Manage Webhook -> Recent Deliveries by checking the Response for 200, which means the Github event (commit) has been processed successfully.
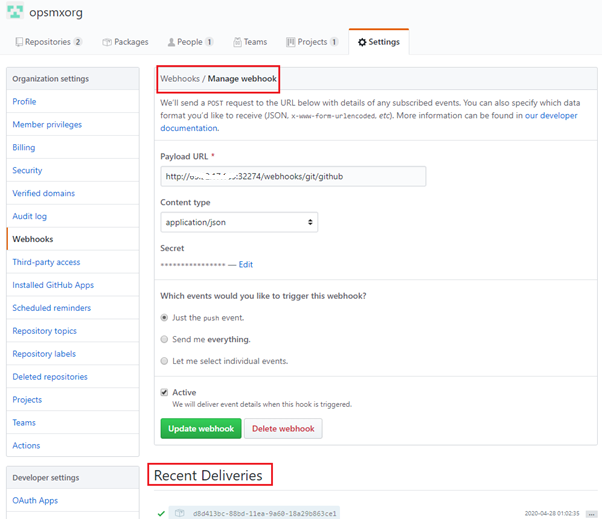
Verification of the Spinnaker deployments on Kubernetes – Check Manage WebHooks
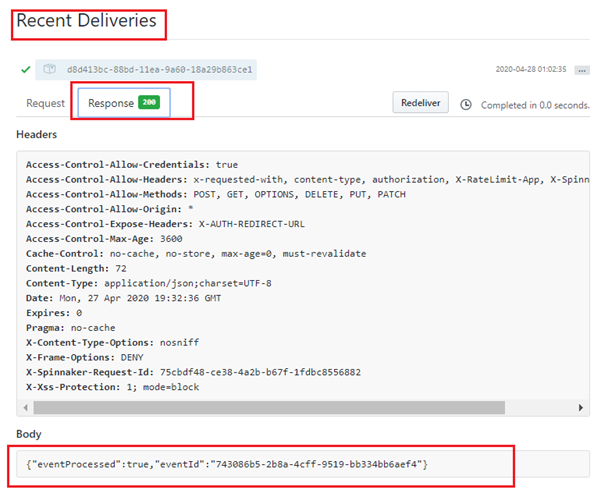
Verification of the Spinnaker deployments on Kubernetes -Recent Deliveries
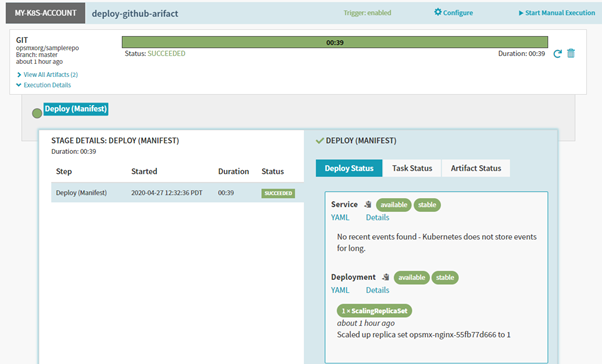
Ensure the Deploy(manifest) stage is executed successfully as shown below:

Spinnaker Deploy Manifest executed successfully
And see the subsequent result in the Kubernetes cluster as below:
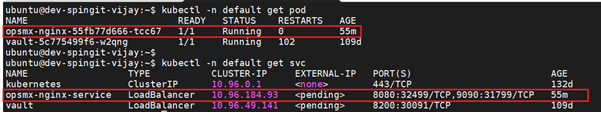
Spinnaker deployments on Kubernetes cluster
OpsMx is a leading provider of Continuous Delivery solutions that help enterprises safely deliver software at scale and without any human intervention. We help engineering teams take the risk and manual effort out of releasing innovations at the speed of modern business. For additional information, contact OpsMx Support.
