Authenticate Spinnaker deployments via SAML using Jumpcloud as IDP (Identity Provider)
Introduction
Security Assertion Markup Language (SAML) is a standard for logging users into applications based on their sessions in another context. This single sign-on (SSO) login standard has significant advantages over logging in using a username/password:
Advantages of using SSO
- No need to type in credentials
- No need to remember and renew passwords
- No weak passwords
The scope of this guide is how to set up SAML authentication on Spinnaker using JumpCloud as the (IDP)Identity Provider. This integration is not yet readily supported in the open-source Spinnaker version and OpsMx has added value while extending the support for the customers who want to run Spinnaker with a highly secured environment. JumpCloud securely manages and connects employee identities to Spinnaker, its underlying Kubernetes pods, configuration files, YAML files, etc. based on the user roles. JumpCloud is a central source of authentication, authorization, and management of employees and all to which they require access.
To know more about Spinnaker authentication with SAML using JumpCloud as the Identity Provider please read the following articles from Jumpcloud which are excellent to get you started:
Pre-Requisites
- Spinnaker application is already installed.
- JumpCloud account with required users is available.
- Admin access with the Jumpcloud to add the Spinnaker application is available.
Setting up JumpCloud Account
- Navigate to https://console.jumpcloud.com/
- Click signup and register the new account.
Note: Once a free account is created, we can use it for 10 Users, if you need to add more than this number need to purchase the JumpCloud license depending on the number of users required.
Configuring Spinnaker Authentication using SAML with Jumpcloud as IDP
To configure the Spinnaker application to use the JumpCloud SAML application as IDP for authentication you need to do the following things:
- Configure a Spinnaker application in the JumpCloud.
- Configure Halyard with the Jumpcloud SAML application
Let us discuss these steps in detail.
-
Configure a Spinnaker application in the JumpCloud
- Login to JumpCloud as the administrator (https://console.jumpcloud.com/) using the administrator login credentials.
- Configure Spinnaker as a new SSO Application.
(Navigate to SSO —>Add Application —> Custom SAML App).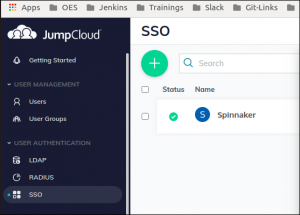
Login to JumpCloud as administrator

- Provide a suitable name in the “Required Name” field (Ex: Spinnaker) for the custom application.
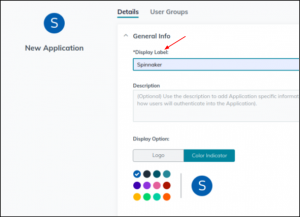
Provide the required name for the custom application.
- Provide the SSO Configuration, by setting up the following:
-
- IdP Entity ID – Example: spind
- SP Entity ID – Entity ID here should match with the Issuer ID in Spinnaker Halyard, Example: spind
- ACS URL – This is the EndPoint to which JumpCloud will send the SAML responses. For Spinnaker it is basically the Gate URL + /saml/SSO. Example: https://test-spin.opsmx.com/gate/saml/SSO
Note: The endpoint URL should be followed by: /saml/SSO.
- Save the application.
- Once the Application is saved you will get the certificate.pem and the metadata.xml, save both of them into your local which will be needed for the spinnaker configuration.
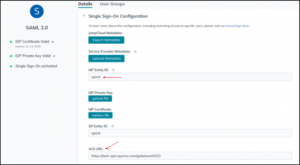
SSO configuration details
-
- Add the required users to access the Spinnaker Application.
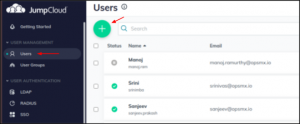
Add Users
-
Configure the Halyard to use the Spinnaker Jumpcloud SAML Application for Authentication
-
- Create a SAML keystore for Spinnaker.
Configure the Spinnaker to use the Jumpcloud as SAML Authentication provider.hal config security authn saml edit \--keystore $KEYSTORE_PATH \--keystore-alias saml \--keystore-password $KEYSTORE_PASSWORD \--metadata $METADATA_PATH \--issuer-id $ISSUER_ID \--service-address-url $SERVICE_ADDR_URLSERVICE_ADDR_URL is the Spinnaker gate endpoint URL.- Enable SAML authentication.
hal config security authn saml enable - Apply the halyard changes
hal deploy apply - Once changes are applied, you can verify Spinnaker authentication. It should take you to the JumpCloud login page and should be able to authenticate to Spinnaker successfully.
So now that you have learned about how to use the JumpCloud service as the Identity Provider(IDP) to provide SAML authentication in your Spinnaker deployments. You can always go ahead and try it yourself. Please do share your experiences with us and also feel free to post your queries in the comment section below. We hope that we can help you troubleshoot your problems.
If you want to know more about authentication in Spinnaker, or know general about the Spinnaker Continuous Delivery tool you can request a demonstration. To do so please book a meeting with us.
OpsMx is a leading provider of Continuous Delivery platform that helps enterprises safely deliver software at scale and without any human intervention. We help engineering teams take the risk and manual effort out of releasing innovations at the speed of modern business. For additional information, contact us
