SAML Authentication on Spinnaker using GSuite
Purpose
SAML SSO provides flexibility to login once against an Authentication source and maintain user session across multiple applications of an organization. It eliminiates the need to remember user credential for every individual system and avoids logging into them individually.
The scope of this guide is how to setup SAML authentication on Spinnaker using GSuite SAML app.
Pre-Requirements
- Spinnaker 1.16.2
- GSuite with valid users
- You should be Administrator on GSuite to configure SAML app
Configuring Spinnaker Authentication using GSuite SAML
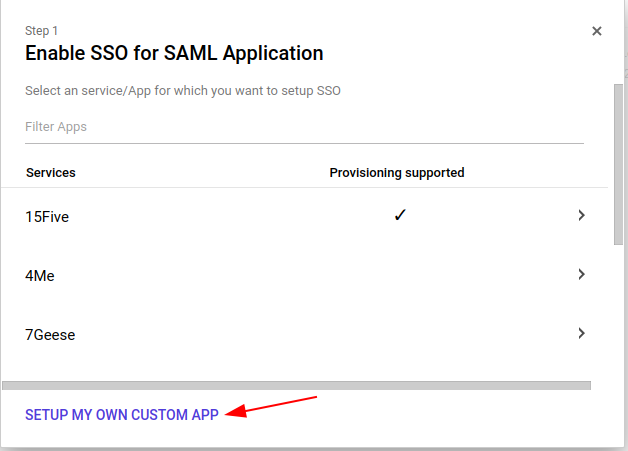
- Add an application in GSuite SAML apps for Spinnaker, then
- Configure Halyard using some of the settings from GSuite SAML application
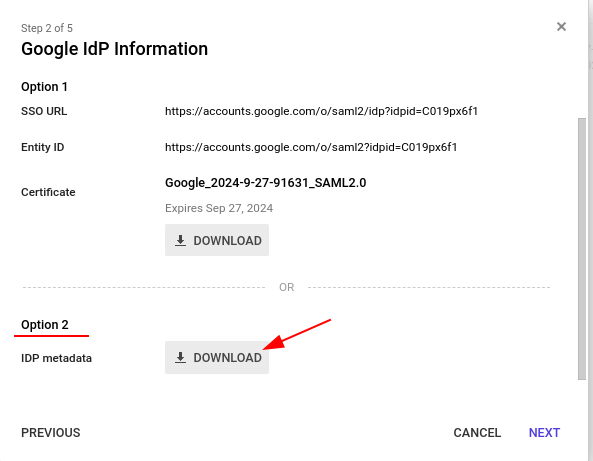
Adding Spinnaker application in GSuite SAML
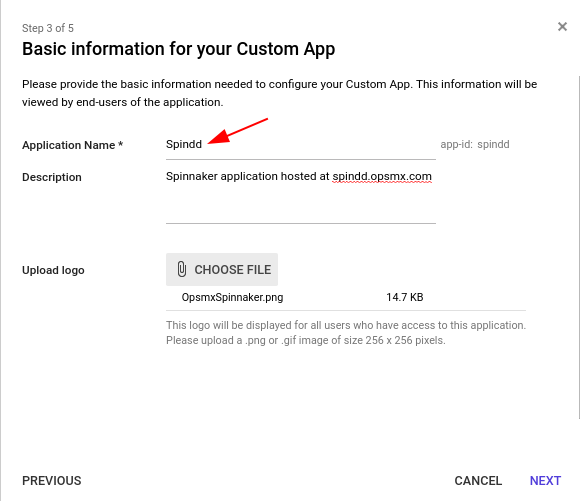
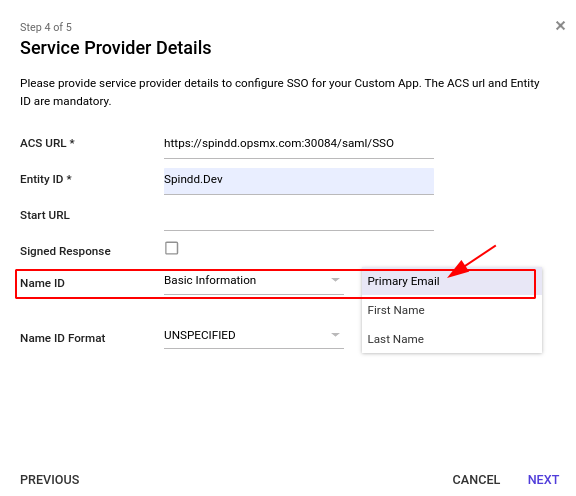
- ACS URL: https://spindd.opsmx.com:30084/saml/SSO (Note the suffix)
Note: The Name ID value here will be mapped as the User name on Spinnaker application. You can set it to Primary Email, First Name or Last Name as shown in the picture.
1. Create a SAML key store for Spinnaker
KEYSTORE_PATH=/home/spinnaker/.hal/saml/saml.jks keytool -genkey -v -keystore $KEYSTORE_PATH -alias saml -keyalg RSA -keysize 2048 -validity 10000
spinnaker@halyard-57f8d6f8dc-74xbp:~/.hal/saml$ cat vars.saml KEYSTORE_PATH=/home/spinnaker/.hal/saml/saml.jks KEYSTORE_PASSWORD=xxxxxx # Password entered in the step just above. METADATA_PATH=/home/spinnaker/.hal/saml/GoogleIDPMetadata-opsmx.io.xml SERVICE_ADDR_URL=https://spindd.opsmx.com:30084 ISSUER_ID=Spindd.Dev #This value should be same as Entity ID value entered in GSuite SAML setup screen. spinnaker@halyard-57f8d6f8dc-74xbp:~/.hal/saml$ source vars.saml spinnaker@halyard-57f8d6f8dc-74xbp:~/.hal/saml$ hal config security authn saml edit \ --keystore $KEYSTORE_PATH \ --keystore-alias saml \ --keystore-password $KEYSTORE_PASSWORD \ --metadata $METADATA_PATH \ --issuer-id $ISSUER_ID \ --service-address-url $SERVICE_ADDR_URL
spinnaker@halyard-57f8d6f8dc-74xbp:~/.hal/saml$ hal config security authn saml enable
spinnaker@halyard-57f8d6f8dc-74xbp:~/.hal/saml$ hal config security authn oauth2 disable
spinnaker@halyard-57f8d6f8dc-74xbp:~/.hal/saml$ hal deploy apply
After successful login to Spinnaker, checking the below URL can tell you of the attributes successfully mapped.
{
"email": "sagayaraj.d@opsmx.io",
"username": "sagayaraj.d@opsmx.io",
"firstName": null,
"lastName": null,
"roles": [],
"allowedAccounts": [
"k8s-qa-spin",
"saga-azure-account"
],
"enabled": true,
"authorities": [],
"accountNonExpired": true,
"credentialsNonExpired": true,
"accountNonLocked": true
}

spinnaker@halyard-57f8d6f8dc-74xbp:~/.hal/saml$ hal config security authn saml edit \ --user-attribute-mapping-first-name firstName \ --user-attribute-mapping-last-name lastName # List of possible attributes we can associate are here. We can eliminate any of the attribute that is not required. spinnaker@halyard-57f8d6f8dc-74xbp:~/.hal/saml$ hal config security authn saml edit \ --user-attribute-mapping-username userName \ --user-attribute-mapping-email email \ --user-attribute-mapping-first-name firstName \ --user-attribute-mapping-last-name lastName --user-attribute-mapping-roles memberOf \ --user-attribute-mapping-roles-delimiter ,
{
"email": "sagayaraj.d@opsmx.io",
"username": "sagayaraj.d@opsmx.io",
"firstName": "Sagayaraj",
"lastName": "David",
"roles": [],
"allowedAccounts": [
"k8s-qa-spin",
"saga-azure-account"
],
"authorities": [],
"enabled": true,
"accountNonExpired": true,
"credentialsNonExpired": true,
"accountNonLocked": true
}
Troubleshooting
Problem 01: Following error appears immediately after accessing Spinnaker deck url
403. That’s an error. Error: app_not_configured_for_user Service is not configured for this user. Request Details That’s all we know.
Solution: Possibly the App is not turned ON in GSuite. Enable it
Problem 02: Following error appears immediately after entering username and password. 403. That’s an error. Error: app_not_configured_for_user Service is not configured for this user. Request Details That’s all we know.
Solution: The Issuer ID on Halyard configuration does not match with the Entity ID on GSuite SAML apps. Make sure they are configured with same value.
Problem 03: During Spinnaker authentication process, after entering username and password web page is looping back and forth continuously.
Solution: Most likely the the ACS URL in GSuite and SERVICE_ADDR_URL in Halyard are pointing to Gate URL only – https://spindd.opsmx.com:30084. Rember on Halyard it should be Gate URL and on GSuite, ACS URL should be ‘Gate URL + /saml/SSO’
Problem 04: 500. That’s an error. There was an error. Please try again later. That’s all we know.
Solution: Most likely the SAML app is GSuite is deleted by someone. Verify and re-configure SAML app in GSuite.
